HELLO, I'M
Vouth Sovann
Information Technology Specialist
Vouthanack Sovann
TS/SCI Cleared Veteran
M.S. in Cybersecurity
Master of Business Administration
B.S. in Computer Studies
B.S. in Information Systems (2024)
A.A.S. in IT and Networking
A.A. in Financial Management
Certificate in Programming Essentials
Certificate in Digital Forensics
Certificate in System Administration
Active Certifications
Certifed Information Systems Security Professional
Information Systems Security Engineering Professional
Information Systems Security Management Professional
Certified Cloud Security Professional (CCSP)
Certified Information Security Manager (CISM)
CompTIA Secure Infrastructure Expert (CSIE)
CompTIA Secure Analytics Expert (CSAE)
CASP+ | CySA+ | Cloud+ | Security+ | | Pentest+ | Project+
Certified Ethical Hacker (CEH)
Certified Network Defense Architect (CNDA)
(240) 513-8125
About
Highly qualified IT professional, United States Veteran, and dedicated scholar of cyber security. Earned numerous certifications to include Certified Information Systems Security Professional, CompTIA Advanced Security Practitioner, Security+, Cloud+, Project+, Certified Ethical Hacker, (Big Data) Splunk Core Certified User Training, and Certified Network Defense Architect. Acquired hands-on experience in penetration testing skills in a lab environment with cutting- edge simulated systems.
Driven by intellectual challenge, leverages advanced business acumen with a solutions-oriented leadership style to optimize technology opportunities and support teams. Proficient in researching a company’s security system, network structure, and possible penetration sites to identify opportunities for corrective actions and security upgrades. Identify and triage security events, collaborate with the incident response team, monitor security operations, perform threat hunting activities, and execute risk analysis initiatives to harden agency systems. Contribute to mission-critical initiatives with an exemplary work ethic.
Education
WHAT I’VE LEARNED
Experience
WHERE I’VE WORKED
University of Maryland - University College Adelphi, MD
Master of Business Administration
Master of Science; Cybersecurity
Bachelor of Science; Computer Studies
DeVry University
Manhattan, NY
Bachelor of Science; Information Systems (est 2024)
Associate of Applied Science; IT and Networking
Certificate; Programming Essentials
Community College of the Air Force
Maxwell AFB, AL
Associate of Arts; Financial Management
Certifications
Certified Information Systems Security Professional - (CISSP) - ISC2
Information Systems Security Engineering Professional
(CISSP-ISSEP) - ISC2
Information Systems Security Management Professional
(CISSP-ISSMP) - ISC2
Certified Cloud Security Professional (CCSP) - ISC2
Certified Information Security Manager (CISM) - ISACA
Certified Ethical Hacker (CEH) - EC-Council
Certified Network Defense Architect (CNDA) - EC-Council
Advanced Security Practicioner (CASP+) - CompTIA
Core Certified User - Splunk
CompTIA Secure Infrastructure Expert (CSIE)
CompTIA Secure Analytics Expert (CSAE)
CompTIA CASP+ | Cloud+ | CySA+ | Pentest+ | Project+ | Security+

U.S. Department of Commerce
Accounting Technician (2007 - 2008)
-
Keyed millions of dollars in check deposit transactions.
-
Corrected and reconciled billings, collections and adjustments.
-
Prepared monthly and weekly reports for assigned A/R accounts.
-
Prepared and examined financial records for annual fiscal year audit.
-
Verified accuracy of accounts receivable incoming negotiable instruments.

U.S. Air Force
Finance Technician (2002 - 2006)
-
Presented briefings to military personnel on pay and travel entitlements.
-
Disbursed daily cash payments while deployed in Iraq.
-
Accurately processed thousands of travel vouchers.
-
Resolved finance related questions for military members.
-
Coded thousands of payroll documents for military and civilian members.
-
Prepared accountability records and reports.
-
Accounted for millions of dollars in cash and negotiable instruments.
-
Certified and processed payment and collection vouchers.
-
Maintained accuracy of appropriated funds, accounting records and files.
-
Led travel pay section in processing and payment of travel claims for military members in DTS.
Purdue Northwest University - IvyTech
Valparaiso, IN
Certificate in Cybersecurity; Digital Forensics
Certificate in Cybersecurity; System Admininistration
Certificate in Cybersecurity; Artificial Intelligence (est. 2024)
Pending Certifications
AWS - Solutions Architect – Associate | AWS Security – Specialty
Certified Information Systems Auditor (CISA)
Certified in Risk and Information Systems Control (CRISC)
Certified Hacking and Forensic Investigator (CHFI)
Cisco Certified Network Associate (CCNA) – CyberOps
Cisco Certified Network Professional (CCNP) – Security
Google Professional Cloud Architect | Google Professional Security Engineer
Nutanix Certified Professional – Multi-Cloud Infrastructure
Splunk Enterprise Security Certified Admin

U.S. Department of State
IT Specialist (2011 - Present)
-
Exercised collaborative and cross-functional teamwork throughout technical project planning and delivery for sophisticated communications and information systems while serving in United States Embassies across Central and South America, Europe, Africa, Middle East and Asia. Act as the sole IT officer due to mastery of new and emerging technologies.
-
Employ advanced technical acumen in maintaining satellite, leased-line, cryptographic material, databases, computers, digital imaging, HVAC, and diesel generator equipment. Ensured business continuity, disaster recovery, and seamless operations.
-
Coached, trained, and mentored personnel in the correct utilization of computer interfaces, software, and hardware.
-
Employed efficiency in troubleshooting, practicing root cause analysis, and resolving IT deficiencies and issues.

Central Intelligence Agency
Finance Administrator (2009 - 2011)
PM Support Officer (2008 - 2009)
Finance Administrator
Achieved a promotion due to accomplishing value-added contributions, action-oriented leadership, and a commitment to superior standards of excellence.
-
Displayed optimal levels of productivity in processing daily financial transactions, check collections, weekly deposits, and the coding of a high volume of data.
-
Ensured accuracy, confidentiality, and regulation compliance while producing bi-weekly salary payments for personnel.
PM Support Officer
Assessed CIA contractor data to identify opportunities for corrective actions and process improvements, resulting in more effective workforce management and operations.
-
Developed and delivered hands-on training curriculum on leading-edge applications in support of information collection. Also designed and deployed the office’s website geared specifically to customers and stakeholders.
-
Architected automated survey tools for collecting a high volume of vital customer information.
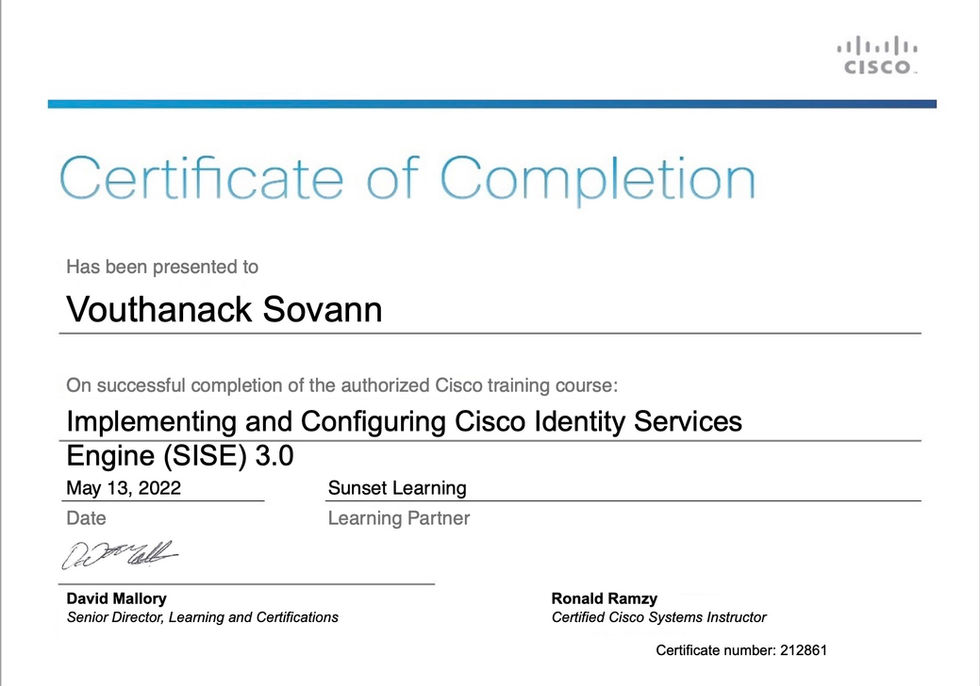
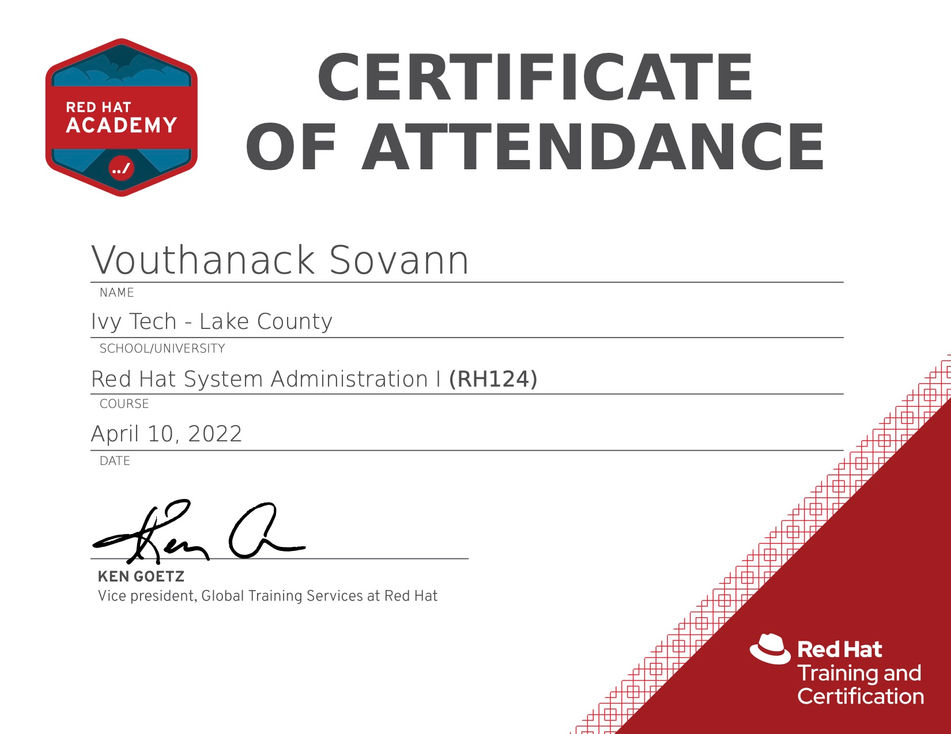
Training Certificates
Skills & Languages
WHAT I BRING TO THE TABLE
Digital Forensics | Vulnerability Assessment | Penetration Testing | Troubleshooting Disaster Recovery | Cross-Functional and Collaborative Teamwork | Interpersonal Communication | Cloud-Based Services and Security | System Documentation | Regulatory Compliance | Data Loss Prevention | In-Depth Security Investigations | Incident Response Tactics | Classified Environments External Data Monitoring | Malware Eradication | Network Security Threat Elimination | Digital Evidence Collection | Root Cause Analysis | IoT Devices | Linux | Python
English
Khmer
Awards
WHERE I SHINE
Devry Deans List (Fall '21 / Spring '22 / Spring '23)
Exceptional Performance Awards
Iraq Campaign Award
Airman of the Month
Interests
OUT OF OFFICE
Spartan Races
Marathons
Tennis
Vehicle Repair
Mentoring
Cooking
Computer Repair
Crypto Mining
Training and Exposure
Skills/Experience/Exposure
-
Adobe Express
-
Anaconda
-
Arduino
-
Burp Suite
-
CAINE
-
Canvas
-
Cisco Net Academy
-
Cisco Packet Tracer
-
CompTIA CertMaster
-
DEFT
-
Draw.io
-
FCrackZip
-
HxD
-
Linux (Fedora /Ubuntu)
-
Microsoft Office 365
-
Microsoft Server 2012/2016
-
Microsoft Windows 10 / 11
-
NETLAB+
-
Red Hat Academy
-
SE Toolkit
-
Spyder
-
Virtual Box
-
Visio
-
Visual Studio 2019
-
VMWare
-
Word | Excel | Powerpoint | Visio | Publisher
-
TNT Crypter
Devry Skillport
EC-Council Code Red
TryHackMe
CONTINUOUS LEARNING
Penetration Testing
-
Capture The Flag
-
Hashcat
-
John the Ripper
-
Metasploit
-
Nmap
-
Password Cracking Fundamentals
-
Wireshark
Hacking Scenarios
-
ARP Spoofing and MiTM Attacks
-
Backdooring with Netcat
-
Client Side Exploitations
-
Covering Your Tracks
-
Creating and Installing SSL Certificates
-
Cryptography
-
DNS Footprinting
-
Enumeration
-
Evading IDS
-
Metasploit Framework Fundamentals
-
Mobile Hacking
-
Network Analysis
-
Packet Crafting with Scapy
-
Password Cracking with JTR and Hashcat
-
Reconnaissance with Hping
-
Reconnaissance with Nmap, Zenmap, and Masscan
-
Scanning Methodology
-
Social Engineering Attacks with SET
-
System Hacking
-
Understanding Buffer Overflows
-
Understanding SQL Commands and Injections
-
VNC as a Backdoor
-
Vulnerability Scanning with OpenVAS
-
Web Pentesting
-
Web-Based Hacking
-
Windows Security Account Manager
Forensics Tools
-
ADF Solutions
-
Autopsy
-
Cellebrite
-
CSI Linux
-
EnCase
-
FTK
-
Oxygen
-
Software/Hardware write blockers
Forensic Scenarios
-
Chain of Custody Form Processing
-
Creating a Forensic Image
-
Data Carving
-
Email Analysis
-
Evidence Intake Form Processing
-
File Hashing and Hash Analysis
-
File Systems
-
Internet Browser Forensics
-
IoT Forensics
-
Keyword Search and Analysis
-
Live Acquisition
-
Live Forensics
-
Log Capturing and Interpretation
-
Metadata and Link File Analysis
-
Mobile Forensic Analysis
-
Pagefile Analysis
-
Password Cracking
-
Picture File Analysis
-
Recycle Bin Forensics
-
Registry Forensics
-
Steganography and Alternative Data Streams
-
Timeline Analysis
Cisco Cyber Ops
-
SciTE
-
Security Onion
-
Identify Running Processes
-
Exploring Processes, Threads, Handles, and Windows Registry
-
Create User Accounts
-
Using Windows PowerShell
-
Windows Task Manager
-
Monitor and Manage System Resources in Windows
-
Working with Text Files in the CLI
-
Getting Familiar with the Linux Shell
-
Linux Servers
-
Locating Log Files
-
Navigating the Linux Filesystem and Permission Settings
-
Tracing a Route
-
Introduction to Wireshark
-
Using Wireshark to Examine Ethernet Frames
-
Using Wireshark to Observe the TCP 3-Way Handshake
-
Exploring Nmap
-
Using Wireshark to Examine a UDP DNS Capture
-
Using Wireshark to Examine TCP and UDP Captures
-
Using Wireshark to Examine HTTP and HTTPS Traffic
-
Exploring DNS Traffic
-
Attacking a mySQL Database
-
Reading Server Logs
-
Creating Codes
-
Hashing Things Out
-
Encrypting and Decrypting Data Using OpenSSL
-
Encrypting and Decrypting Data Using a Hacker Tool
-
Examining Telnet and SSH in Wireshark
-
Certificate Authority Stores
-
Snort and Firewall Rules
-
Convert Data into a Universal Format
-
Regular Expression Tutorial
-
Extract an Executable from a PCAP
-
Interpret HTTP and DNS Data to Isolate Threat Actor
-
Isolate Compromised Host Using 5-Tuple
-
Investigating a Malware Exploit
-
Investigating an Attack on a Windows Host